All new Registrations are manually reviewed and approved, so a short delay after registration may occur before your account becomes active.
Pass the SSL Labs Test on Apache2 (Mitigate CRIME & BEAST attack, Disable SSLv2 and Enable PFS)
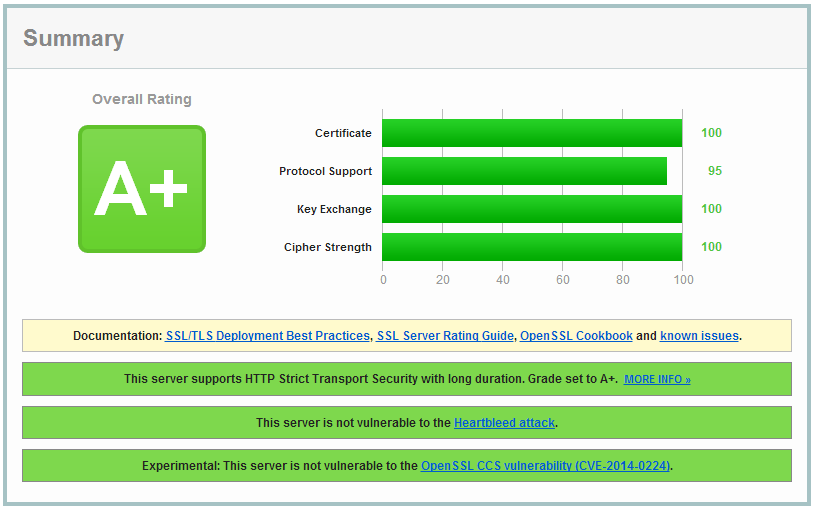
This tutorial shows you how to get an A on the SSL Labs test using the Apache2 webserver. We do this by disabling CBC based chipers to mitigate the BEAST attack, disabling SSL Compression to mitigate the CRIME attack, disable SSLv2 and below because of vulnerabilities in the protocol and we will enable Perfect Forward Secrecy when possible. This way we have a future proof ssl configuration and we get an A on the Qually Labs SSL Test.
This tutorial is also available for NGINX
You can find more info on the topics by following the links below:
Make sure you backup the files before editing them!
Mitigate the BEAST attack
In short, by tampering with with an encryption algorithm's CBC - cipher block chaining - mode's, portions of the encrypted traffic can be secretly decrypted. More info on the above link.
To mitigate it, we are going to edit the Apache settings in the file /etc/apache2/mods-enabled/ssl.conf (On Ubuntu/Debian) or in /etc/httpd/conf.d/httpd.conf (On RHEL/CentOS).
What we need to do is disable all CBC chipers. If you have a version of OpenSSL lower than 1.0.1c then your only option is to use the RC4 chiper because TLS 1.2 support is added in 1.0.1c, but the RC4 chiper also has known weaknesses in it.
The lines below first have TLS 1.2 chipers for TLS 1.2 clients to pick those up, and at the end it has the RC4 chiper. It also enables the HonorChiperOrder option which uses the servers order of chipers instead of letting the client choose. (More on HonorChiperOrder - More info on SSLChiperSuite.
SSLHonorCipherOrder On
SSLCipherSuite ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-RC4-SHA:ECDHE-RSA-RC4-SHA:ECDH-ECDSA-RC4-SHA:ECDH-RSA-RC4-SHA:ECDHE-RSA-AES256-SHA:RC4-SHA:!MD5:!aNULL:!EDH
If you run an Apache and OpenSSL Version that do not support TLS 1.2 you can also use this config because it will then only use the RC4 chiper.
The rest of this tutorial can be read on Raymii.org
@mpkossen If you please, this could go on LEB as a full tutorial?
















Comments
Nice tutorial.
BTW, I saw it on /r/sysadmin on reddit.
Added to my list :-)
GnuTLS: Syntax error parsing priorities string at: +AES-256-GCM
What to do with it?
Use OpenSSL.
@Raymii Thanks for the tut but fyi this post & the nginx article at least contain multiple typos where cipher === chiper!
@FFFlip I've also got some email about that, and fixed it.
@Raymii took me way too long to realise it wasn't something else I didn't know about! :P
Why I need to use OpenSSL
@dnwk because GNUtls gives you errors?
Ok.... I want to solve the error.....
Great stuff!
As said, make sure to use OpenSSL instead of GNUtls. My tutorial was tested against OpenSSL.