All new Registrations are manually reviewed and approved, so a short delay after registration may occur before your account becomes active.
DDOS Protection for Website with vDDoS Proxy Protection & vDDoS Layer4 Mapping
Install vDDoS Proxy Protection & vDDoS Layer4 Mapping to Antiddos for Web Server
Hi everyone, in this tutorial I have two servers: One for simulate an Denial of Service by attack tools and One for running a website to become a target.
On server target, I have the following 4 cases: (4 domain pointing to 1 hosting LAMP run Joomla CMS source web)
1> http://cloudflare-vddos-web.i-com.cf:80 (Traffic proxied through Cloudflare's CDN & vDDoS Proxy)
2> http://cloudflare-web.i-com.cf:8080 (Traffic proxied through Cloudflare's CDN)
3> http://vddos-web.i-com.cf:8081 (Traffic proxied through vDDoS Proxy)
4> http://direct-web.i-com.cf:8082 (Direct traffic)
[root@www ]# netstat -lntup
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:8080 0.0.0.0:* LISTEN 864/httpd
tcp 0 0 0.0.0.0:8082 0.0.0.0:* LISTEN 864/httpd
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 5747/nginx: master
tcp 0 0 0.0.0.0:8081 0.0.0.0:* LISTEN 5747/nginx: master

OK, Step 1: on attacker server I will check the contents of the website in each case by curl tool:
4> http://direct-web.i-com.cf:8082 (Direct traffic)
[root@attacker ~] curl -L http://direct-web.i-com.cf:8082
<!DOCTYPE html>
<html lang="en-gb" dir="ltr">
<head>
<meta name="viewport" content="width=device-width, initial-scale=1.0" />
<meta charset="utf-8" />
<base href="http://direct-web.i-com.cf:8082/" />
<meta name="generator" content="Joomla! - Open Source Content Management" />
<title>Home</title>
<link href="/index.php?format=feed&type=rss" rel="alternate" type="application/rss+xml" title="RSS 2.0" />
<link href="/index.php?format=feed&type=atom" rel="alternate" type="application/atom+xml" title="Atom 1.0" />
<link href="/templates/protostar/favicon.ico" rel="shortcut icon" type="image/vnd.microsoft.icon" />
<link href="http://direct-web.i-com.cf:8082/index.php/component/search/?Itemid=435&format=opensearch" rel="search" title="Search joomla" type="application/opensearchdescription+xml" />
<link href="/templates/protostar/css/template.css?b07c885111c1b29246c60f35646efe84" rel="stylesheet" />
<link href="//fonts.googleapis.com/css?family=Open+Sans" rel="stylesheet" />
<style>
</head>
=> You can see the site's html code by curl because without challenge of vDDoS Proxy
2> http://cloudflare-web.i-com.cf:8080 (Traffic proxied through Cloudflare's CDN)
[root@attacker ~] curl -L http://cloudflare-web.i-com.cf:8080
<!DOCTYPE html>
<html lang="en-gb" dir="ltr">
<head>
<meta name="viewport" content="width=device-width, initial-scale=1.0" />
<meta charset="utf-8" />
<base href="http://cloudflare-web.i-com.cf:8080/" />
<meta name="generator" content="Joomla! - Open Source Content Management" />
<title>Home</title>
<link href="/index.php?format=feed&type=rss" rel="alternate" type="application/rss+xml" title="RSS 2.0" />
<link href="/index.php?format=feed&type=atom" rel="alternate" type="application/atom+xml" title="Atom 1.0" />
<link href="/templates/protostar/favicon.ico" rel="shortcut icon" type="image/vnd.microsoft.icon" />
<link href="http://cloudflare-web.i-com.cf:8080/index.php/component/search/?Itemid=435&format=opensearch" rel="search" title="Search joomla" type="application/opensearchdescription+xml" />
<link href="/templates/protostar/css/template.css?b07c885111c1b29246c60f35646efe84" rel="stylesheet" />
<link href="//fonts.googleapis.com/css?family=Open+Sans" rel="stylesheet" />
<style>
</head>
=> Cloudflare default does not challenge you + Without challenge of vDDoS so you can also see the site's html code by curl
1> http://cloudflare-vddos-web.i-com.cf:80 (Traffic proxied through Cloudflare's CDN & vDDoS Proxy)
[root@attacker ~] curl -L http://cloudflare-vddos-web.i-com.cf:80
<html><body><script type="text/javascript" src="/aes.min.js" ></script><script>function toNumbers(d){var e=[];d.replace(/(..)/g,function(d){e.push(parseInt(d,16))});return e}function toHex(){for(var d=[],d=1==arguments.length&&arguments[0].constructor==Array?arguments[0]:arguments,e="",f=0;f<d.length;f++)e+=(16>d[f]?"0":"")+d[f].toString(16);return e.toLowerCase()}var a=toNumbers("f9c5842006d8c3552b5dba4d25c2c8b2"),b=toNumbers("ad396baa8934584ef179ae25af75b6b2"),c=toNumbers("4d5571fddc3d46ce22abf0636806b0aa");document.cookie="vDDoS="+toHex(slowAES.decrypt(c,2,a,b))+"; expires=Thu, 31-Dec-37 23:55:55 GMT; path=/";location.href="http://cloudflare-vddos-web.i-com.cf/?d=1";</script></body></html>
=> Can't pass challenge of vDDoS because "curl is NOT a full browser. It is just a library that is used for communicating with servers, using HTTP, FTP, et cetera. It does not do neither rendering nor parsing. For this functionality, you would need a full browser with JavaScript engine."
3> http://vddos-web.i-com.cf:8081 (Traffic proxied through vDDoS Proxy)
[root@attacker ~] curl -L http://vddos-web.i-com.cf:8081
<html><body><script type="text/javascript" src="/aes.min.js" ></script><script>function toNumbers(d){var e=[];d.replace(/(..)/g,function(d){e.push(parseInt(d,16))});return e}function toHex(){for(var d=[],d=1==arguments.length&&arguments[0].constructor==Array?arguments[0]:arguments,e="",f=0;f<d.length;f++)e+=(16>d[f]?"0":"")+d[f].toString(16);return e.toLowerCase()}var a=toNumbers("7187a67c06c01ec70fa705e69c985366"),b=toNumbers("d5ae1b31d36068285e139d0823c8f490"),c=toNumbers("2849732479830475c796dd532ebee31e");document.cookie="vDDoS="+toHex(slowAES.decrypt(c,2,a,b))+"; expires=Thu, 31-Dec-37 23:55:55 GMT; path=/";location.href="http://vddos-web.i-com.cf:8081/?d=1";</script></body></html>
=> Can't pass challenge of vDDoS because "curl is NOT a full browser...Like mentioned"
Finish Step 1.
Step 2: I used a tool to try to request flood on 4 website target (something tools like HTTP benchmark or DOS, SYN, HTTP flood... you often use)
4> http://direct-web.i-com.cf:8082 (Direct traffic)
[root@attacker ~] Attack ->->->-> http://direct-web.i-com.cf:8082
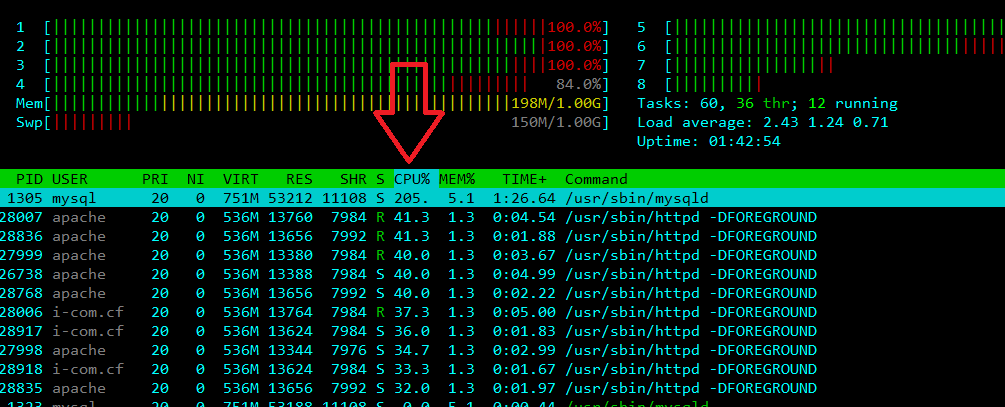
=> High load cpu + ram + bw ... (nothing challenges attacker)
2> http://cloudflare-web.i-com.cf:8080 (Traffic proxied through Cloudflare's CDN)
[root@attacker ~] Attack ->->->-> http://cloudflare-web.i-com.cf:8080
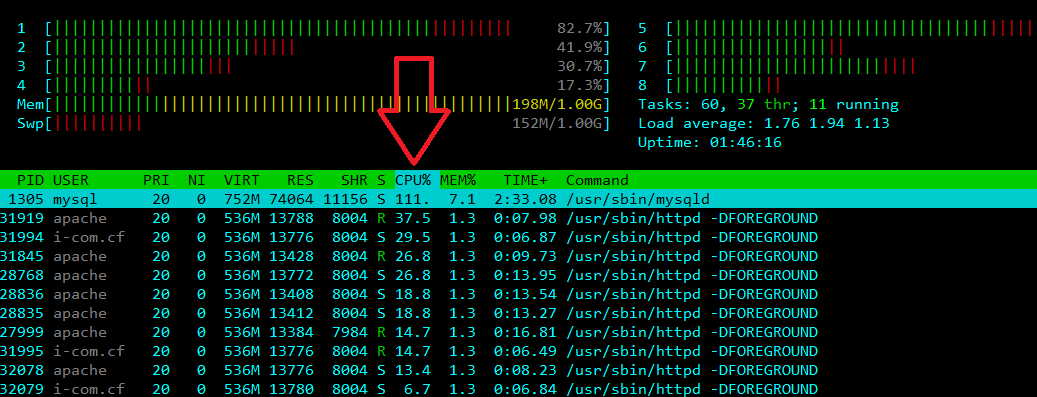
=> Use Attack tools Layer 3-4 is nothing happens but with Attack tools Layer 7 your target will be high load cpu + ram + bw ...
3> http://vddos-web.i-com.cf:8081 (Traffic proxied through vDDoS Proxy)
[root@attacker ~] Attack ->->->-> http://vddos-web.i-com.cf:8081

=> Can't pass challenge of vDDoS Proxy -> Apache httpd daemon is not high load
1> http://cloudflare-vddos-web.i-com.cf:80 (Traffic proxied through Cloudflare's CDN & vDDoS Proxy)
[root@attacker ~] Attack ->->->-> http://cloudflare-vddos-web.i-com.cf:80

=> Can't pass challenge of vDDoS Proxy -> Apache httpd daemon is not high load
The easiest is to use ab tools HTTP benchmark to test:
ab -n100000 -c500 http://direct-web.i-com.cf:8082/ # High load
ab -n100000 -c500 http://cloudflare-web.i-com.cf:8080/ # High load
ab -n100000 -c500 http://vddos-web.i-com.cf:8081/ # Normal load
ab -n100000 -c500 http://cloudflare-vddos-web.i-com.cf:80/ # Normal load
Step 3: Of course, the foregoing is only a test with 1 Attacker Server vs 1 Target Server. What will happen if it is >1000 Attacker Server vs 1 Target Server?
As described, vDDoS Proxy can block all requests send from >1000 Bots, but if your website under too many attack bots -> Your Target server will be high load for transmission handling that challenge. Therefore, you should send that list of >1000 Bots (IP Address/Range of it) to Layer 3-4 and BLOCK/DROP it by something like Hardware Firewall, Iptables, CloudFlare Firewall...
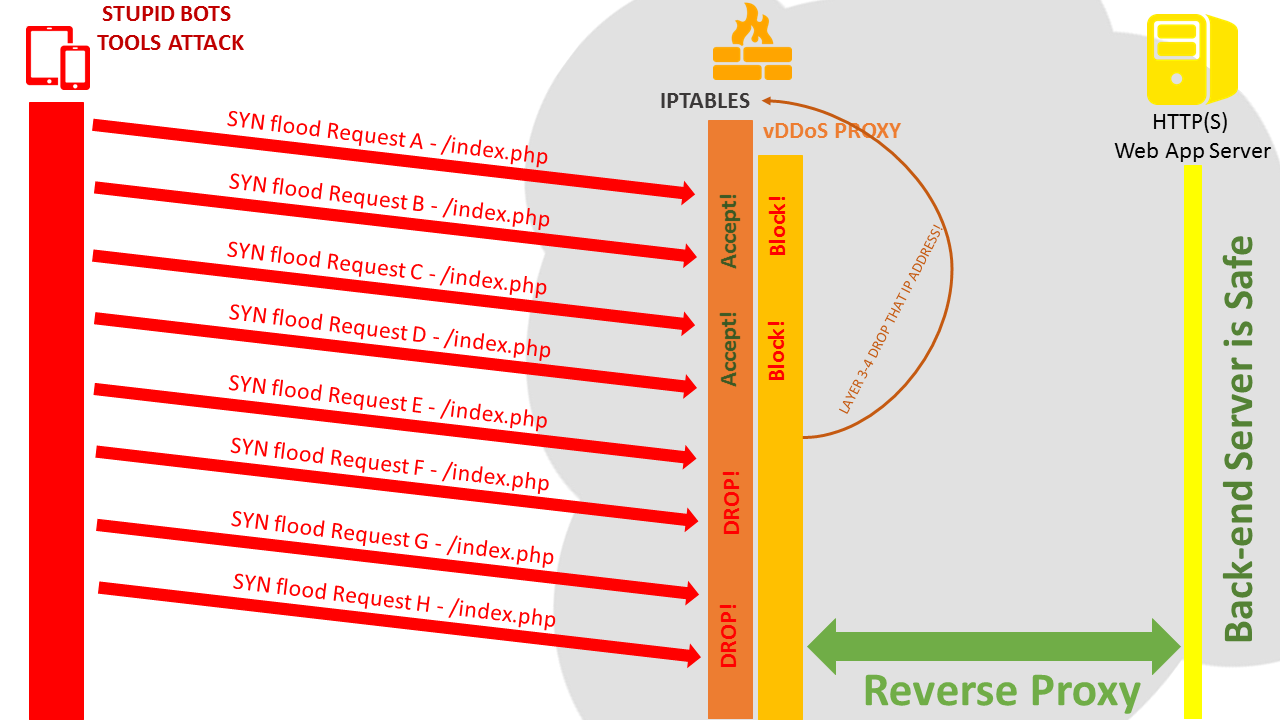
How can we do that?

You can use vDDoS Layer4 Mapping: https://github.com/duy13/vDDoS-Layer4-Mapping
Install:
curl -L https://github.com/duy13/vDDoS-Layer4-Mapping/raw/master/vddos-layer4-mapping -o /usr/bin/vddos-layer4
chmod 700 /usr/bin/vddos-layer4
/usr/bin/vddos-layer4
If you use CloudFlare:
Register account on CloudFlare.com > Add Your Website > Overview > Zone ID
Email > My Setting > API Key > Global API Key > View API Key
If you use CSF:
Homepage: https://configserver.com/cp/csf.html
Install CSF:
cd /usr/src/
wget 'https://download.configserver.com/csf.tgz'
tar -xvf csf.tgz
cd csf
sh install.sh
chkconfig --levels 235 csf on
chkconfig --levels 235 lfd on
Config CSF (as you want):
cd /etc/csf/
sed -i 's/TESTING = "1"/TESTING = "0"/g' /etc/csf/csf.conf
Restart CSF:
csf -r && csf -q && service lfd restart
Use vDDoS-Layer4-Mapping:
/usr/bin/vddos-layer4
(Choose options 2 or 5 as you want)
OK NOW, Step 4: we will repeat step 2, used a tool to try to request flood on all website target again:
3> http://vddos-web.i-com.cf:8081 (Traffic proxied through vDDoS Proxy)
[root@attacker ~] Attack ->->->-> http://vddos-web.i-com.cf:8081
=> Can't pass challenge of vDDoS Proxy -> Apache httpd daemon is not high load.
[root@www ]cat /etc/csf/csf.deny
54.164.194.1
Check Your /etc/csf/csf.deny file => see IP Address of Attacker Server
1> http://cloudflare-vddos-web.i-com.cf:80 (Traffic proxied through Cloudflare's CDN & vDDoS Proxy)
[root@attacker ~] Attack ->->->-> http://cloudflare-vddos-web.i-com.cf:80
=> Can't pass challenge of vDDoS Proxy -> Apache httpd daemon is not high load.
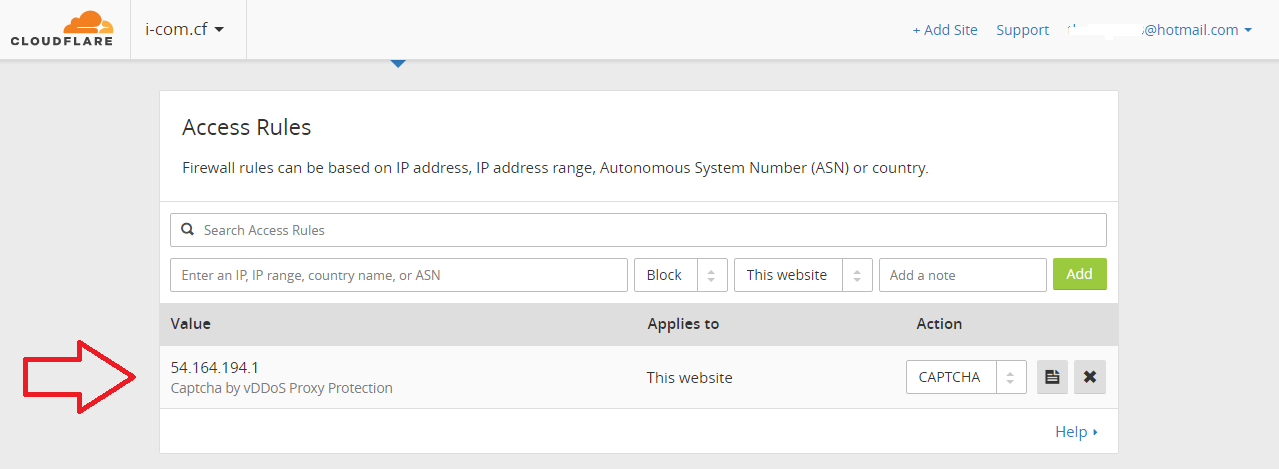
If you use CloudFlare => Check Your Cloudflare Firewall Pages => see IP Address of Attacker Server
Step 5: If you're unlucky, confronted with an DDOS attack unbelievable => you can try use CloudFlare and enable functions Enable Captcha-All-Country Mode in vDDoS Layer4 Mapping. It will enable captcha challenge for 251 countries around the world, although there is a little inconvenient for users but it can keep your site's survival. (Don't forget allow whitelist of botsearch ip range)
Good luck for your site!

















Comments
Very informative post.
smh, this was posted 9 months ago.
Still it's helpful and informative.
I think it is very helpful!
thank you for the help
What a necro.